How to Trade 2 Cards from Biometric Scanners Safely and Efficiently
In today’s rapidly evolving technological landscape, security is a top priority for both individuals and organizations. One of the most advanced methods used for access control and identity verification is biometric scanning. From fingerprint recognition to iris and facial scans, biometric systems are becoming increasingly common. But did you know that you can also trade 2 cards from biometric scanners to enhance security measures further?
In this article, we will dive into the process of trading cards from biometric scanners, exploring how it works, its significance, and the practical steps to ensure smooth implementation. By the end, you will have a thorough understanding of how this advanced feature adds a new layer of protection and flexibility to biometric security.
What Are Biometric Scanners?
Before discussing how to trade 2 cards from biometric scanners, it’s essential to understand what these scanners are and how they work. Biometric scanners are devices used to identify individuals by capturing and analyzing their unique physical characteristics. This technology is typically more secure than traditional methods such as passwords or PIN codes, as it’s based on physical attributes like fingerprints, facial patterns, or retina scans. These characteristics are extremely difficult to replicate, making biometric scanners a robust tool in the realm of security.
Biometric systems are commonly used in sensitive environments such as financial institutions, government agencies, and corporate offices. However, as the technology becomes more accessible, it’s also making its way into consumer devices like smartphones and smart home systems. Now, let’s explore how trading 2 cards from biometric scanners fits into this security landscape.

Here is the unique image representing the concept of biometric scanners based on the content you provided.
What Does It Mean to Trade 2 Cards from Biometric Scanners?
The phrase “trade 2 cards from biometric scanners” refers to the process of exchanging or transferring authentication cards within a biometric security system. These cards serve as an additional layer of verification, complementing the biometric scan. Typically, in a biometric security system, cards or tokens are used alongside biometric data to ensure multi-factor authentication. Trading these cards can refer to switching them between users, systems, or facilities for specific purposes.
By allowing users to trade or exchange these cards, organizations can enhance the flexibility and functionality of their security protocols. The cards might contain data that enables access to certain restricted areas, or they could be used to authorize specific actions, such as signing contracts or approving transactions. The key is that the biometric system ties the card to a person’s identity, verified through the biometric scan, ensuring secure access.
Why Trade 2 Cards from Biometric Scanners?
Trading 2 cards from biometric scanners can offer several significant benefits for security and operational efficiency. Here are some of the key reasons why organizations might choose to implement such a system:
Enhanced Security with Biometric Scanners and Card Trading
Biometric scanners provide a high level of security on their own, but adding card-based verification offers an additional layer of protection. This is especially useful in environments where sensitive data or valuable assets are being protected. By trading 2 cards from biometric scanners between authorized users, organizations can ensure that only verified personnel have access to restricted areas or functions. The combination of biometric and card-based verification minimizes the risk of unauthorized access.
Increased Flexibility for Large Organizations
In large organizations or multi-location facilities, trade 2 cards from biometric scanners allows for enhanced and flexible access control. Employees or authorized personnel can easily exchange cards to access various locations or systems as needed. This streamlined approach eliminates the need for multiple cards or credentials across different departments or buildings. For instance, if an executive requires temporary access to a restricted area for a project, trading cards provides a secure and efficient solution without compromising overall security measures.
Streamlined Operations for Collaborative Environments
Trading cards within a biometric scanner system is not just about security; it’s also about improving operational efficiency. In environments that require team collaboration, such as secure facilities or research labs, trading cards can facilitate joint tasks. Instead of issuing new credentials every time access is needed, trading 2 cards from biometric scanners allows for efficient and secure access management. This saves both time and resources, contributing to smoother operations in complex environments.
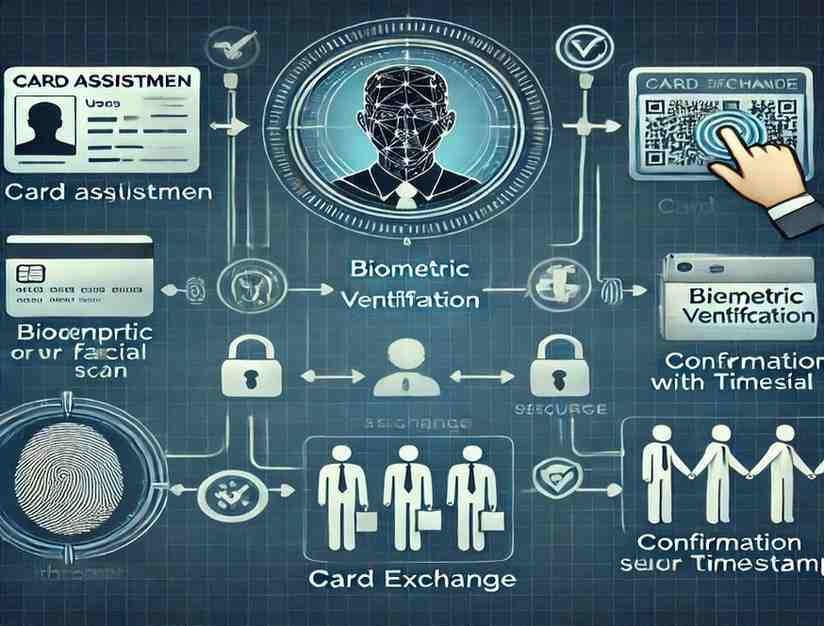
Here is the unique image illustrating the card trading process in a biometric scanner system.
How Does the Trading Process Work?
Now that we’ve covered the advantages of trading 2 cards from biometric scanners, let’s break down how the process works in a typical system. Understanding this process ensures that organizations can adopt this practice safely and effectively.
Card Assignment and Registration
The initial step in trading 2 cards from biometric scanners is to assign each user their respective cards, which are then securely linked to their biometric data. These cards act as an additional layer of authentication, working alongside the user’s biometric credentials, such as fingerprints, facial scans, or retina scans. By linking the card to biometric data, the system ensures that only authorized individuals can access sensitive areas or systems.
In some cases, a user may be issued two cards to provide added flexibility, allowing them to manage multiple access points or departments without needing additional credentials. This setup helps enhance overall security, ensuring smooth and controlled access while maintaining a robust audit trail for accountability.
Biometric Verification
Before a card can be traded, the user must authenticate their identity using the biometric scanner. Whether it’s through a fingerprint, facial scan, or retina scan, the system ensures that the person is authorized to initiate the trade. This verification step is crucial for maintaining security, especially when organizations trade 2 cards from biometric scanners. By confirming the user’s identity with biometrics, the system prevents unauthorized access and ensures that only verified personnel can perform the card trade.
Card Exchange
Once biometric verification is complete, the user can initiate the card trade. Trading 2 cards from biometric scanners can be done electronically, with the system securely transferring access privileges from one user to another. In some setups, the exchange might involve physical cards or tokens, depending on the organization’s security protocols. This process ensures that access is controlled and only authorized personnel can complete the card exchange, enhancing both flexibility and security in managing access to restricted areas or systems.
Confirmation and Audit Trail
Once the card has been traded, the system generates a confirmation that the exchange was successful. This confirmation includes time stamps, user details, and the access privileges associated with the trade. Most systems also generate an audit trail, ensuring accountability and transparency. The organization can review this audit trail at any time to ensure that no unauthorized trades have taken place.
Secure Storage and Management
In any biometric system, it is essential that all card data, biometric credentials, and trade records are stored securely within the system’s database. This ensures that the process of trade 2 cards from biometric scanners is fully protected against potential breaches or tampering. By maintaining strong encryption and access controls, organizations can safeguard sensitive information and ensure that only authorized personnel can view or modify the stored data. This level of security is crucial in preventing unauthorized access and maintaining the integrity of the system.

Here is the unique image highlighting key considerations for implementing biometric scanners with card trading.
Key Considerations for Implementing Biometric Scanners with Card Trading
Implementing a system that allows for trading 2 cards from biometric scanners requires careful planning and execution. Below are key considerations that organizations should keep in mind:
System Compatibility
Before implementing trading 2 cards from biometric scanners, it is crucial to ensure that your biometric scanner system supports this feature. Not all biometric systems are designed to handle card trading directly, and some may lack the functionality to integrate card-based verification. Therefore, it is essential to choose a system that has the card trading capability built into its design. This ensures smooth operation and avoids compatibility issues down the line.
By selecting a system that supports trading 2 cards from biometric scanners, organizations can streamline access management, enhance security, and ensure that authorized personnel can seamlessly trade cards within the system, boosting operational efficiency.
User Training for trade 2 cards from biometric scanners
Proper training is essential for employees or users involved in trading 2 cards from biometric scanners to ensure that the process is executed correctly and securely. Users must be familiar with how the biometric verification works, how to securely initiate and complete a card trade, and what steps to follow in case of any issues or errors. By educating users on the system’s functionality and best practices, organizations can significantly reduce the risk of misuse or mistakes during card trades.
This training also helps users understand the importance of safeguarding sensitive information and adhering to security protocols, ensuring that trading cards from biometric scanners is performed with the highest level of accuracy and safety. Regular training and updates on new features or system changes further ensure that all users remain competent and confident in handling this important security process.
Compliance and Privacy in Biometric Systems
Biometric systems handle highly sensitive personal data, such as fingerprints, facial recognition, and other unique identifiers. Therefore, organizations must ensure compliance with relevant privacy laws and regulations when implementing these systems. It’s crucial that all biometric data and records associated with trade 2 cards from biometric scanners are securely stored and protected. Additionally, only authorized personnel should have access to this information, ensuring that both privacy and security standards are upheld. Properly managing these sensitive records reduces the risk of data breaches and helps maintain trust in the organization’s security protocols.
Access Control Policies
Set clear policies regarding who is authorized to trade cards and under what circumstances. These policies should be communicated to all users to ensure that the card-trading process is consistent and secure.
Security Protocols
To further enhance security, organizations should implement additional security protocols, such as two-factor authentication, for critical card trades. For instance, when a user attempts to trade 2 cards from biometric scanners, they might need to verify their identity through a second method, like an email or SMS confirmation. This added layer of protection significantly reduces the risk of unauthorized access and ensures that only legitimate users can complete the trade. By combining biometric verification with multi-factor authentication, organizations can achieve a higher level of security in their operations.

Here is the unique image illustrating the real-world applications of trading 2 cards from biometric scanners across different sectors.
Real-World Applications for Trading 2 Cards from Biometric Scanners
Biometric scanners with card trading capabilities can be applied in various sectors, from corporate environments to public services. Here are some real-world applications:
Corporate Offices
In large corporations with multiple departments and restricted areas, trading cards from biometric scanners helps streamline access control. This process allows employees, such as executives, IT staff, and security personnel, to gain temporary or cross-departmental access without the need for multiple credentials. For example, if an executive needs temporary access to a secure area, card trading provides a quick and secure solution while maintaining strict security protocols.
The flexibility of trading 2 cards from biometric scanners ensures that only authorized personnel can access sensitive areas, while also creating an audit trail for accountability. This method increases operational efficiency by reducing the need for multiple access cards and still requires biometric verification for enhanced security.
Healthcare Facilities
In hospitals and clinics, safeguarding patient data and controlled substances is of the utmost importance. Biometric scanners with card-trading capabilities provide secure access to sensitive areas, such as medication storage or patient records. By implementing systems that allow healthcare professionals to trade 2 cards from biometric scanners, facilities can ensure that only authorized personnel access these critical areas. This approach not only enhances security but also ensures accountability through detailed audit trails, providing a clear record of who accessed what and when, thus maintaining a secure and compliant environment.
Government and Military
High-security government facilities and military installations often rely on multi-factor authentication for access control. Trading 2 cards within these environments ensures that only verified personnel can access top-secret or sensitive areas. The ability to trade cards provides additional flexibility without compromising security.
Educational Institutions
Universities and research labs require secure access to specialized areas. Trading 2 cards from biometric scanners allows faculty and researchers to share access to these facilities while maintaining strict control over who enters. This system ensures only authorized individuals can access sensitive areas, facilitating collaborative work without compromising security. With an audit trail for accountability, trading cards from biometric scanners provides flexibility and security, making it an ideal solution for managing access in academic and research environments.
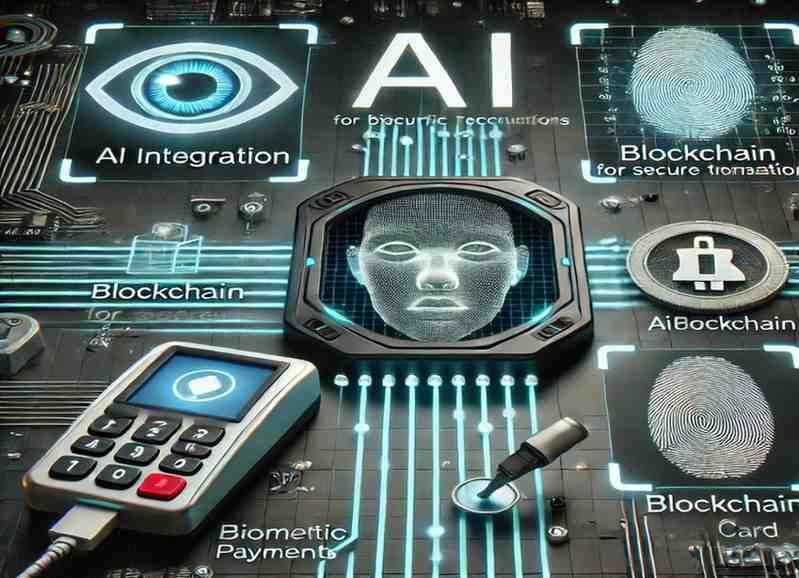
Here is the unique image showcasing future trends in biometric security, highlighting AI integration, blockchain, biometric payments, and advanced modalities.
Future Trends in Biometric Security
The trading of 2 cards from biometric scanners is just the beginning of what’s possible with biometric technology. As biometric systems evolve, we can expect even more advanced features to enhance security and usability. Below are some future trends to watch for:
AI Integration
Artificial Intelligence (AI) is set to revolutionize biometric security by enhancing the efficiency and security of trading 2 cards from biometric scanners. AI can analyze user behavior patterns, detect anomalies, and issue real-time security alerts when something unusual occurs. This capability ensures that the process of trading cards becomes even more secure, minimizing risks while providing faster, more accurate authentication and response times in biometric systems.
Blockchain for Secure Transactions
Integrating blockchain technology into biometric systems could enhance security when trading 2 cards from biometric scanners. Blockchain would create an immutable ledger, ensuring that all card trades are verifiable and secure. This added layer of protection ensures that no card trades can be altered or tampered with, providing a transparent and reliable record of every transaction, further enhancing trust and accountability in access control systems.
Biometric Payments
Biometric verification for payments is an emerging trend being explored across various industries. In the future, trading 2 cards from biometric scanners could be expanded to authorize secure financial transactions. This would allow users to trade cards within the biometric system to approve payments, adding an extra layer of security. By combining biometric verification with card trading, businesses can ensure that financial transactions are securely processed, reducing the risk of fraud or unauthorized access.
This innovative use of biometric technology could revolutionize payment systems, making them both safer and more efficient.
Advanced Biometric Modalities
While fingerprint and facial recognition are the most common biometric methods today, other modalities, such as voice recognition and heartbeat patterns, are being developed. These advanced modalities could be integrated into future systems to provide even more secure verification options for trading cards.
FAQ: Trade 2 Cards from Biometric Scanners
1. What does it mean to trade 2 cards from biometric scanners?
Trading 2 cards from biometric scanners refers to exchanging or transferring access credentials between authorized users within a biometric security system. The cards are typically linked to biometric data, ensuring secure and verified access to restricted areas or systems.
2. How does biometric verification work in card trading?
Before a card trade is initiated, users must authenticate their identity using a biometric scanner. This could involve fingerprint, facial recognition, or retina scans, ensuring that only authorized individuals can complete the trade.
3. What are the benefits of trading 2 cards from biometric scanners?
This method enhances security by combining biometric verification with card-based authentication. It offers flexibility for access control, reduces the need for multiple credentials, and maintains a detailed audit trail for accountability.
4. In what settings can card trading with biometric scanners be useful?
Trading 2 cards from biometric scanners is particularly useful in corporate offices, healthcare facilities, government institutions, universities, and research labs. It allows for secure, flexible access control across various departments and restricted areas.
5. How does card trading improve operational efficiency?
Card trading simplifies access management, allowing temporary or cross-departmental access without issuing new credentials. It saves time and resources, making operations smoother in secure environments where collaboration is essential.
6. What role does AI play in trading cards from biometric scanners?
AI can analyze user behavior, detect anomalies, and enhance security in real-time. It ensures that trading 2 cards from biometric scanners is efficient and secure, reducing risks and improving response times to security threats.
7. How does blockchain technology enhance card trading in biometric systems?
Blockchain can create an immutable ledger of card trades, ensuring that each trade is verifiable and tamper-proof. This adds another layer of security, making card trading more transparent and reliable.
8. What measures should be in place for secure card trading?
Organizations should use two-factor authentication, audit trails, and regular security protocols when trading 2 cards from biometric scanners. This ensures that only verified individuals can complete trades and access secure areas.
The Power of Biometric Scanners with Card Trading
In conclusion, the ability to trade 2 cards from biometric scanners opens up a world of possibilities for enhancing security and operational efficiency. By combining biometric verification with card-based authentication, organizations can implement a multi-factor system that offers flexibility, accountability, and protection. Whether in corporate offices, healthcare settings, or government facilities, trading cards from biometric scanners is a powerful tool for managing access and ensuring security.
As technology continues to evolve, we can expect even more exciting developments in biometric security, making these systems an essential component of future security strategies.




Leave a Review